In the early 90’s, when the consumer “World Wide Web” as it exists today was just getting started, it was apparent to many that we would soon be facing some serious security issues. The original Internet was built on trust: trust between universities and research institutes and the security-through-obscurity which came with being the only entities (military and select institutions) that were part of the original Internet. Even in the late nineties, there were not enough people or things connected to the Internet to cause more than mild disruptions should someone figure out how to cause problems. And they did. The Melissa and ILOVEYOU viruses showed email providers and corporations how fragile their servers could be and caused billions of USD in losses worldwide. Productivity was lost but business went on as usual since paper was still used by an overwhelming percentage of organizations.
Living without paper
The underlying technology of the Internet has not changed dramatically since its inception. What has changed is the speed with which we communicate and the number of devices connected to the Internet. We live in a world where almost all facets of our lives are affected in some way by this ubiquitous digital plumbing we call “The Internet”. As has been recently demonstrated, we can no longer travel or even get necessary healthcare without our devices being online and functioning. With the advent of autonomous cars and the Internet of Things (Iot) there will be almost nothing analog left. Security experts have been warning about proper security and security debt for the last two decades. The time to protect ourselves is yesterday.
Solutions
It’s clear that humans have a bias against long-term threats. Cybersecurity is a long-term threat and needs to be dealt with accordingly. This means a true strategy must be created to deal with the long-term effects of being connected full-time to a global cyber-weapons platform. The following are some necessary steps that all organizations need to take to start to solve this problem:
- Move cybersecurity outside of IT;
- Increase cybersecurity spend to a double-digit percentage of the overall budget (independent of IT);
- Engage expert guidance to tune out vendor noise and determine what is most effective from a people, process and technology perspective;
- Identify security-friendly employees across the organization and develop them;
- Embed cybersecurity into the culture;
- Embrace cybersecurity as a business driver rather than a business inhibitor;
- Ensure visibility of security metrics on (at least) a monthly basis.
Consequences
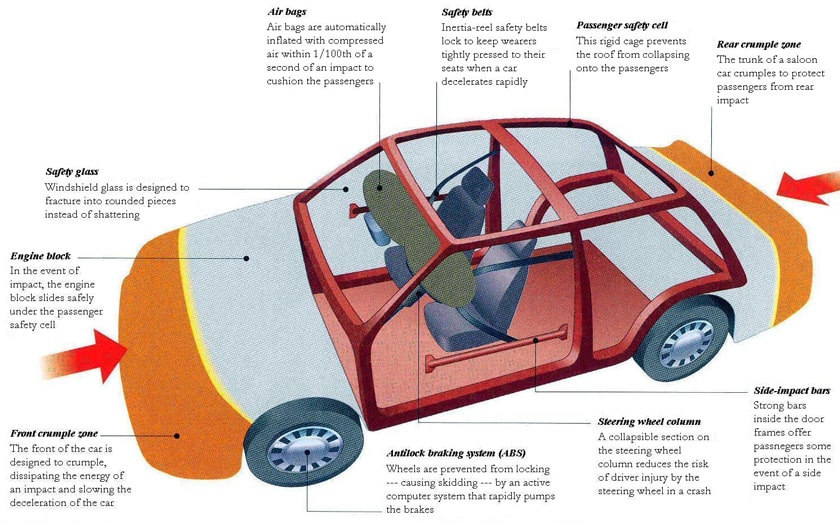
Cybersecurity today is analogous to automobile safety. Consider a moderately mature approach to cybersecurity to be the same as wearing seat belts in a car. Seat belts have been around since the 50’s but were not required in all vehicles in the US until 1968. Many countries did not legislate their use until the 80’s. Today we have airbags, ABS and improved safety systems which have increased automobile safety tremendously. In cyber, we are in the pre-seat belt legislation era. Many organizations are not even using seat belts. If organizations continue to drive at high speed on the Internet without changing their attitude towards safety, the consequences will be fatal.


Recent Comments