Top 5 Reasons Why the Enterprise is Getting Cybersecurity Wrong
The recent Russian hacking operation has once again laid bare the fallacy that the enterprise and government are doing cybersecurity right. Many people are wondering: how are these large entities getting it wrong?
Obviously, large organizations are the biggest targets, containing the most sensitive information, and they will constantly be tested. However, these agencies also have access to the strongest resources. Which begs the question: why are cybersecurity breaches of this scope continuing to occur? Are enterprises too confident in their protocols and technology, or are they too laissez-faire in their deterrence of digital threats? These cyber teams need to be right 100 percent of the time, and the bad guys just have to get it right once, right? Well, there’s more to the story.
What We Know About The SolarWinds Breach
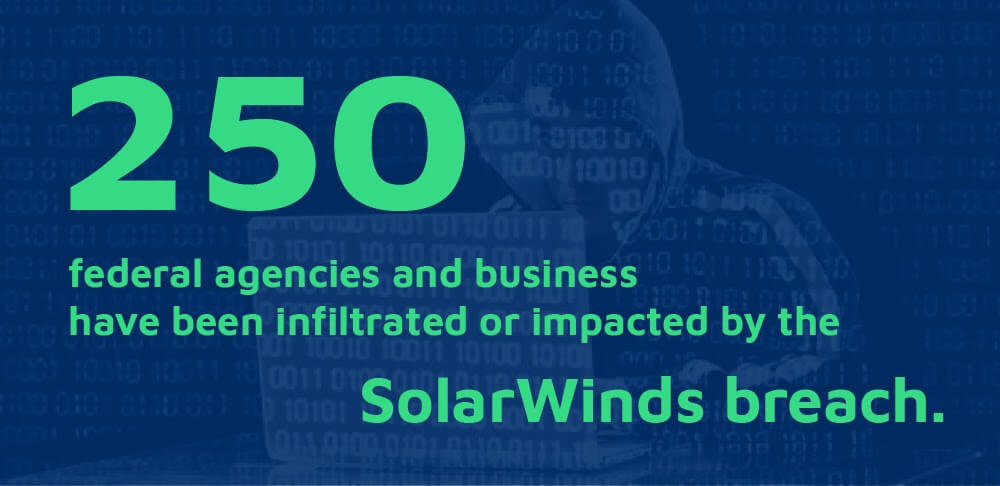
It is now estimated that up to 250 federal agencies and businesses have been infiltrated or impacted, including the Treasury, State, Commerce, and Energy Departments.
Russia’s SVR intelligence service is now widely believed to be the responsible actor in this cybersecurity breach. This same agency was also to blame for the federal cyber attacks in 2014 and 2015 during the Obama administration. Unfortunately, cybersecurity officials are still not able to pinpoint exactly what the SVR’s goal was with this attack. At this time, there is a lack of knowledge about what information and data were accessed and/or stolen.
The start of this SolarWinds breach has been traced back to as early as October 2019. Last week, CrowdStrike, another security company, revealed they were also a hacking target — however, they have stated that their systems were not penetrated. The breach was discovered by the security company, FireEye late last year.
However severe, this breach is not a total surprise to some. Several former SolarWinds employees have come out since the attack and said that best security practices have been cut and reduced in an effort to lower expenses and increase profit margins (SolarWinds’ profit margins in 2019 were $453 million, compared to $152 million in 2010). Most of the company’s engineering has been outsourced to Eastern European countries like Poland and the Czech Republic. This is a much more common practice than people know.
If I had to pin cybersecurity on one issue, it’s lack of visibility and/or context. However, there are other, less-obvious reasons that most enterprises get cyber wrong.
Here’s Why Enterprise Keeps Failing at Cybersecurity
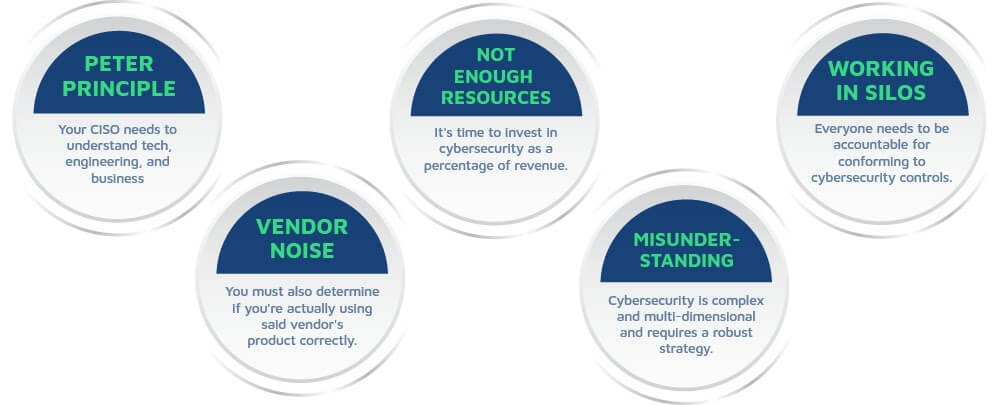
- Peter Principle – Promoting cyber leaders that are not capable or not yet ready to lead. Typically this has been someone who might have had some IT experience, and they’ve been thrust into this role with little training or actual cybersecurity experience.
- Vendor noise – One of the biggest problems in cybersecurity, vendors are all promising to “block all attacks” or be the silver bullet that finally brings order to chaos, it’s almost always a lot of marketing BS.
- Not enough resources – This is a chronic problem across companies of all sizes. The team is too small and the budget is almost non-existent.
- Working in Silos – This is the “it’s IT’s problem” perspective, where the cybersecurity department is passing the buck, or the organization acts as a set of independent entities versus one cohesive team with a clear mandate across all units.
- Misunderstanding of what a real cybersecurity program entails – This is a culmination of the previous four points. There is no easy solution here…cybersecurity is complex and multi-dimensional and requires a robust strategy.
So what steps do organizations of all sizes need to take in order to reimagine cybersecurity, with strength and sound practices? First, admit a flawed philosophy — followed up with new hard-and-fast guidelines to better combat internal malpractice.
Some recommended solutions are below, which correspond to the list above:
- Your CISO needs to understand tech, engineering, and business — and have proven experience with operationalizing security programs (not just conducting audits or giving commands without results).
- You should do a deep security vendor review to determine what actual outcomes you’ve gained from using your current cybersecurity vendors, both from a services and product perspective. You must also determine if you’re actually using said vendor’s product correctly.
- It’s time to invest in cybersecurity as a percentage of revenue. Period. No organization will survive the next 5-10 years without this strategy.
- Break down the silos between the different departments. Cyber needs to be embedded into the entire culture. Appointing a few resources to look after cyber in a 1:5000 ratio is not cutting it. Everyone needs to be accountable for conforming to cybersecurity controls. Departments should be KPI’d based on incidents and loss.
- Passing an audit is not cybersecurity. Beautiful presentations with empty data cannot tell you that you are secure. It takes all of the above to begin building a cybersecurity program, and if you ask your CISO to provide information on the program, they should be able to give real-time information about the state of your controls and overall visibility.
Looking for Trusted Cybersecurity Services?
If you’re looking for more guidance on how to move your cybersecurity program forward, CDG can help. Founded in 2016 by cybersecurity expert Lou Rabon, Cyber Defense Group was designed to address the growing demand for experienced cybersecurity consulting for innovative cloud-native and cloud-reliant organizations. CDG’s commitment to Outcomes-Based Security enables them to fully protect your environment while delivering desired business outcomes in an agile environment. Get in touch, and see what results are possible for your organization.

