Welcome 2020
It’s 2020! Not just a new year, but a new (perceived) decade*.
The 20s will see cybersecurity as one of the most fundamental pieces of digital strategy in the business landscape.
Organizations can no longer delay cybersecurity and privacy initiatives, as the threats increase and regulations grow tighter. Below are some thoughts on what this new decade will bring for your organization, and best defense practices for security and privacy in 2020.
*The decade technically ends on Dec 31, 2020.

Rising Cyber Crime, Vulnerabilities, and The Expense to Businesses
Cybercrime is the greatest threat to every organization today. The facts are breathtaking: There were 5,183 breaches reported in just the first nine months of 2019, exposing 7.9 billion records. Note that this is the number of REPORTED breaches. Based on our experience, the likely number of breaches is at least 10x that number.
These numbers also do not indicate what type of records were breached. Leaked email addresses, for instance, are much less intrusive than leaked health records. A number of these breaches came from large brands with trusted names. Information is Beautiful has a great graphic representation of these breaches by year.
These astronomical numbers are only going to increase, but the irony is that this increases the phenomenon of “breach fatigue”. Breach fatigue is essentially complacency and inaction when faced with the reality that organizations must protect themselves. Breaches are sometimes a “victimless crime” to consumers, but businesses face real consequences if cyber and privacy risk is not addressed.
The reality is this: Organizations must commit a percentage of their budget to a proper cybersecurity and privacy program or face an existential crisis.
Iranian Cyber Attacks
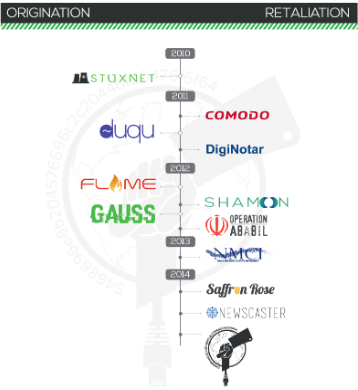
A recent drone strike that killed one of Iran’s most powerful military leaders has given increased attention to potential cyberattacks by Iran. The Iranian cyber capability has been well-documented, including back in 2014 with Cylance’s Operation Cleaver report.
The take-away from this activity is that foreign actors have well-documented hooks into a wide variety of industries. While a large and noisy cyberattack may be imminent, the reality is that a series of smaller attacks on soft business targets which provide essential services would sow more fear, and likely be much more disruptive. This is why all businesses have a responsibility to commit to a cybersecurity program.
2020 Areas of Focus
Luckily, there is hope, and there are solutions for improving cybersecurity posture.
The very first thing individuals and organizations must do for themselves is to commit to a base level of cyber “hygiene.” Most people have ingrained habits to keep themselves clean and healthy, such as flossing teeth, taking the stairs instead of the elevator, etc. Cybersecurity is no different.
Basic cyber hygiene for individuals includes things like:
- Enabling Multi-Factor Authentication (MFA) everywhere you log in,
- Using a password vault for storing the copious amount of passwords used daily,
- Staying educated on the privacy and security settings of all the devices we are using.
For businesses, proper cyber hygiene for 2020 should include a focus on:
- Incident Response
- Logging and Monitoring
- Vulnerability Management
- Governance (such as policies and procedures)
- Third-Party Risk Management
- Security Awareness and Training
- Secure System Development Lifecycle (SSDLC)
Compliance

California’s CCPA privacy regulation took effect on January 1, 2020. While imperfect, it is a sign of what’s to come in the US as the regulatory environment tightens. The CCPA is modeled on the European General Data Protection Regulation (GDPR) and gives consumers certain rights as it relates to their personal information. Most of the current regulations are not prescriptive regarding data protection. This means that organizations must determine what standards, if any, to conform to for data protection.
Our recommendation is to align with the ISO27001, as it is an international standard and has all of the necessary aspects to prove cybersecurity commitment externally. What is certain is that, without a proper cybersecurity strategy, companies are exposed to regulatory actions if they do not meet the standard of “reasonable” cybersecurity.

An Elite Group of Highly-Vetted Cyber Professionals
We can help.
Rapid growth does not require you to compromise on security. CDG continues to provide “Security at Speed” so that your organization can confidently go to market with the latest technologies on the most advanced platforms. We continue to advise, lead, and protect our clients with the following services:
vCISO Subscription Packages
CDG is committed to protecting your business by providing seasoned industry experts to deliver tested and effective cybersecurity strategies to reduce the likelihood and impact of cyber attacks.
An effective cybersecurity program protects the modern enterprise, by aligning security investment with company objectives. CDG will develop tailored security programs that reduce risk, increase security, enable faster sales cycles, and open up regulated markets.
- vCISO Core – Most suited to clients who need occasional strategic security advisory services.
- vCISO Committed – Suited to clients who need strategic assistance building a custom security program, including compliance and operational security.
- vCISO Complete – Ideal for clients who are looking fora fully-outsourced security team that can build a security program from scratch, or mature an existing security program.
Incident Response Services
At CDG we believe no company should go out of business due to a security incident or breach. We have developed a rapid response capability to respond to advanced threats, including nation-state attacks.
- Emergency Incident Response (IR) – For clients who believe they have been compromised and need emergency assistance with the utmost discretion.
- Compromise Assessments – For organizations that require certainty that their operating environments are clean and compromise-free, along with recommendations on addressing areas of weakness.
- Incident Retainer and Readiness – Preparation, training and plan- development for clients who want to proactively prepare for cyber attacks.
Cloud Security Services
Rapid growth and scaling does not mean compromising on security. CDG is committed to providing “Security at Speed” for high growth, rapidly evolving and innovative organizations.
- Active Cloud Defense – Proactive 24×7 defense of next-generation Kubernetes and Serverless technologies, with continuous monitoring of high-risk cloud configurations
- Secure Cloud Engineering – A subscription service to our bench of highly qualified security engineers who will architect, implement, and validate your cloud security.
Please contact us if you’d like more information regarding our services.
Wishing you health, prosperity, and success in 2020!
– The CDG Team

